Politics
Nationwide Government System Outage Paralyzes Public Services
ODTN News broadcaster Roshan Khan
OTTAWA, ON —
Chaos is unfolding across the country today as multiple government systems simultaneously go offline, halting access to essential services and leaving both citizens and officials scrambling for solutions.
The outage, which began mid-morning, has taken down public service portals, ID verification systems, and critical internal government platforms. The disruption is affecting everything from driver’s licence renewals and passport applications to benefits processing and municipal permitting.
“We’ve never seen something on this scale before,” said a senior official at the Ministry of Digital Affairs, speaking on condition of anonymity. “It’s not just the public-facing systems — the internal tools our staff rely on are also unresponsive.”
Nationwide Disruption
In major cities including Toronto, Vancouver, and Halifax, long lines are forming outside government offices as residents attempt to complete services in person, only to be turned away or told to return at a later date. Social media platforms are overflowing with reports of missed appointments, cancelled travel plans, and critical service delays.
“I took the morning off work to get my passport updated and now they’re saying they can’t even see my application,” wrote one frustrated user on Threads. “It’s like the whole government disappeared.”
Authorities Urge Calm
Federal officials are urging Canadians to remain patient while technical teams work to identify and resolve the issue. So far, no timeline has been given for the restoration of services.
Public Safety Minister Valérie Lacroix addressed the nation from Ottawa early this afternoon, saying:
“We are treating this as a matter of national priority. All necessary resources have been deployed to bring systems back online as quickly and safely as possible.”
Cause Still Unknown — Or Just the Beginning?
While the federal government has not confirmed whether the outage is the result of a cyberattack, multiple security analysts note that the scale and simultaneous nature of the disruptions could point to a coordinated incident rather than a routine technical failure.
Some cybersecurity experts are now suggesting that the outage could represent something more troubling — a deliberate “capability test” by hostile actors.
“When public portals and internal systems fail together, that’s already suspicious,” said Dr. André Michaud, a cybersecurity researcher at Laurentian Institute. “But when it happens without obvious ransom demands or immediate damage, you have to consider the possibility that someone is mapping our limits — seeing how far they can go before we push back.”
For now, Canadians across the country are left waiting — in lines, on hold, and online — for the lights to come back on in their government’s digital systems.
Covering where tech meets policy and the gaps in between. — Jordan Okeke
ODTN News’ Ayaan Chowdhury contributed to this report.
Politics
Government Stabilizes Systems, But Trust Gap Remains

September 26, 2025 — After days of disruption fueled by cyber incidents and disinformation campaigns, federal officials confirmed today that critical systems have been stabilized. While the immediate crisis appears to be under control, experts warn that the public trust gap exposed during the turmoil may prove harder to repair.
From Disruption to Stability
Technical teams reported that the low-level beaconing attempts detected earlier this week — signs of adversaries probing for re-entry — have been mitigated. “We’ve deployed layered defenses across all networks and worked directly with partners to contain the threat,” said a senior cybersecurity official. “At this stage, systems are operational and secure.”
The government also announced new joint coordination cells between the Canadian Centre for Cyber Security (CCCS) and critical infrastructure operators, designed to ensure faster detection and response to future threats.
Disinformation Still Lingers
Even as systems came back online, the viral deepfake of a minister blaming refugees continued to circulate, creating confusion and amplifying tensions. Analysts note that while the technical recovery was swift, the information environment remains volatile.
“Once trust is shaken, even accurate updates are met with skepticism,” said a policy researcher at a Toronto think tank. “Citizens are asking themselves: if systems can be manipulated, what else should we question?”
Public Reaction
At airports, where Canadians had faced biometric and passport scanning delays, operations returned to normal. Yet travelers expressed mixed feelings. “I’m glad the kiosks work again,” said one passenger in Montreal. “But no one explained what really happened. That silence is why people stop believing.”
Looking Forward
Officials emphasized that rebuilding trust will require transparency and communication, not just technical fixes. Proposals under consideration include public briefings on cyber resilience, stronger counter-disinformation campaigns, and expanding digital literacy programs.
For now, Canadians can expect their systems to function reliably — but the aftershocks of doubt may shape debates on cybersecurity, governance, and accountability for months to come.
Covering where tech meets policy and the gaps in between. — Jordan Okeke
ODTN News’ Ayaan Chowdhury contributed to this report.
Politics
Canadians Face Passport Scanning Chaos at European Airports

September 24, 2025 — Canadian travelers attempting to return home today are caught in sudden chaos across multiple European airports as automated passport scanners fail to process Canadian documents.
At Rome Fiumicino Airport, long lines quickly built up this morning after machines repeatedly rejected Canadian passports with a flashing red error. Passengers described scenes of confusion as staff scrambled to divert travelers to slower, manual processing.
“It was a nightmare,” said one Canadian en route to Toronto. “The kiosk rejected me three times before staff waved me into another line. Dozens of us were stuck with no clear guidance.”
Reports of the same issue surfaced in Milan and Naples, where returning Canadians posted frustrated updates on social media about being unable to clear security. One traveler wrote: “Lines are at a standstill. Canadian passports just won’t scan. People are missing flights.”
Authorities Responding
While no official explanation has been provided, airport sources suggested the problem may stem from a temporary biometric synchronization error affecting Canadian documents in European systems. The Canadian Border Services Agency (CBSA) confirmed it is monitoring the situation but did not issue immediate travel guidance.
Impact on Travelers
As of this afternoon, passengers continued to face delays of up to several hours. Airline staff reported families missing connections as the backlog grew. “We’re moving people as fast as we can, but when one country’s passports won’t scan, the whole system slows down,” one gate agent said.
Outlook
The disruption remains, but ODTN News will continue monitoring for updates. Travelers returning to Canada are advised to prepare for longer processing times and consider arriving at airports earlier than usual until systems are confirmed stable.
Covering where tech meets policy and the gaps in between. — Jordan Okeke
Politics
Disinformation Spike: Deepfake of Minister Blaming Refugees Goes Viral
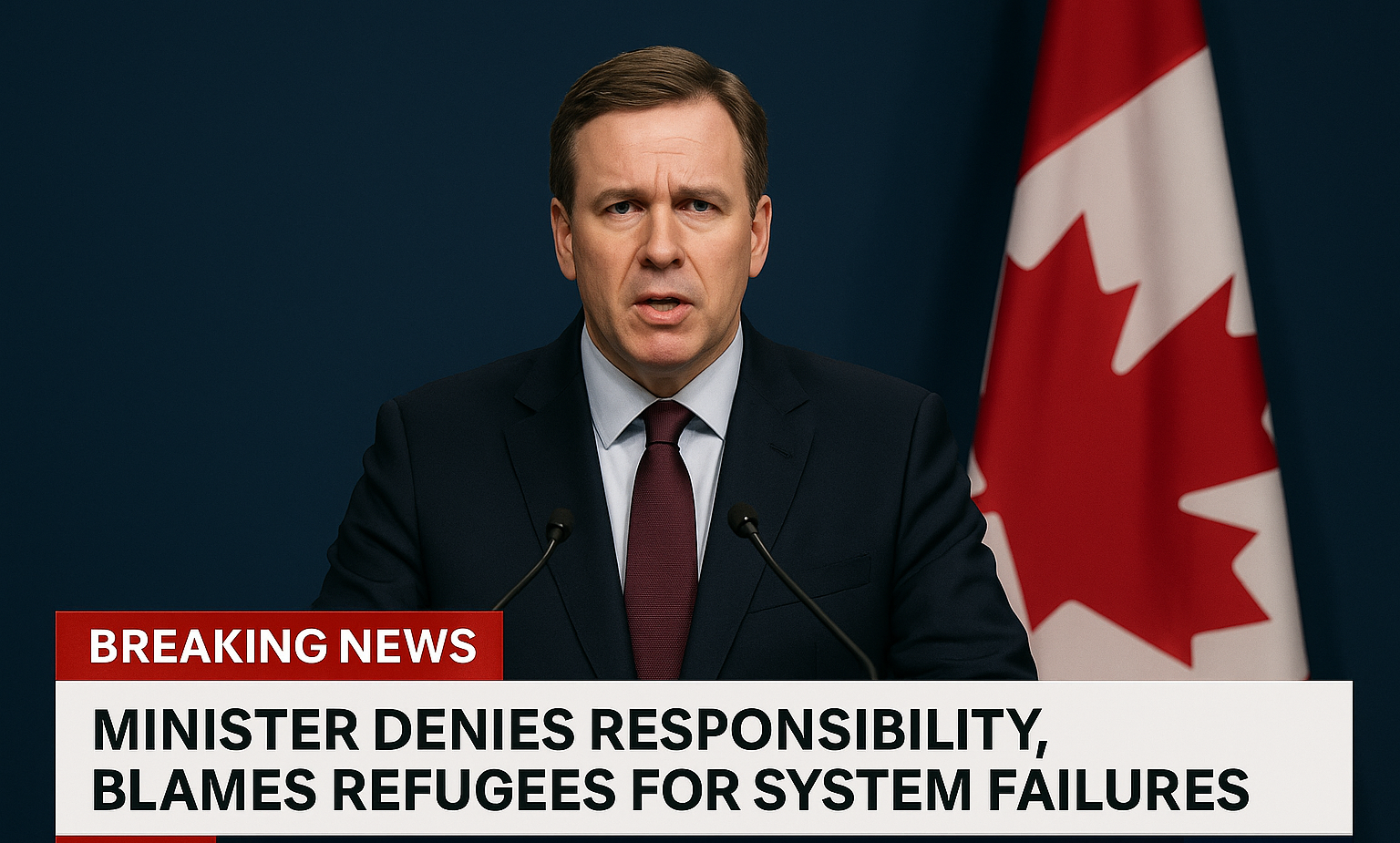
Ottawa, ON — A manipulated deepfake video of a Canadian cabinet minister has spread rapidly across social media today, sparking outrage and fueling false narratives about refugees.
The video, which falsely appears to show the minister blaming refugees for recent social and economic challenges, was quickly identified by cybersecurity analysts as a deepfake disinformation campaign. Despite expert warnings, the clip has already been shared tens of thousands of times across platforms like X, TikTok, and Facebook.
Rapid Spread
Researchers tracking the incident say the video first surfaced early this morning in fringe forums before making its way onto mainstream social media channels. Spreading rapidly, hashtags connected to the video are trending nationally.
“The quality of the manipulation is high enough that casual viewers may not realize it’s fake,” said a threat intelligence analyst. “The speed at which this spread shows how weaponized deepfakes can destabilize public discourse.”
Government Response
The minister’s office issued a statement calling the video “entirely fabricated and malicious.” The statement urged Canadians not to share the clip and confirmed that the case has been referred to federal cybersecurity authorities.
Officials also warned that foreign influence operations have historically used disinformation to sow division in Canada, particularly around refugee and immigration issues.
Public Impact
Community groups expressed concern that the video could inflame tensions. “This kind of content puts refugees at greater risk of harassment,” said one advocacy organization. “It exploits existing fears and undermines social cohesion.”
Looking Ahead
Experts caution that deepfake campaigns are becoming more sophisticated and more frequent. With upcoming policy debates on immigration, disinformation efforts targeting public trust are expected to intensify. For now, fact-checkers and cybersecurity agencies are working to debunk the clip and limit its spread, but the incident highlights how easily trust in democratic institutions can be eroded by synthetic media.
Covering where tech meets policy and the gaps in between. — Jordan Okeke
ODTN News’ Ayaan Chowdhury contributed to this report.
-
 Public8 months ago
Public8 months agoReddit Thread Over ‘Inventory Drift’ Surges as Canadians Vent Over Retail Glitches
-

 Business7 months ago
Business7 months agoAre Canadian Companies Learning from Global Cyber Attacks? Insider Insights into the Secret Downfall of Canadian Businesses
-

 Retail Watch7 months ago
Retail Watch7 months agoCalgary Small Business Hit by Sudden Payment Outage, Sparks Cybersecurity Concerns
-

 Cybersecurity9 months ago
Cybersecurity9 months agoCanadian Airline NorthSky Faces Cyberattack, Disrupting Online Services
-

 Business11 months ago
Business11 months agoCanadian Software Vendor Breach Exposes Cloud Environments Across Energy Sector
-

 Retail Watch8 months ago
Retail Watch8 months agoUnderstaffed and overwhelmed, IT teams face rising pressure as retail digitization accelerates
-

 Business7 months ago
Business7 months agoInsurance Without a Safety Net? Canadian Firms Face Premium Hikes Amid Cyber Liability Crisis
-

 Business6 months ago
Business6 months agosiberX Mart Supply Chain Snarled as Digital Transformation Faces Cyber Threats