Business
Ransomware Attack on Verdance Financial Disrupts Payroll, Business Transfers Across Quebec and Ontario

Montreal, Quebec —
A ransomware attack targeting Verdance Financial earlier this month paralyzed internal systems and disrupted payment operations across Quebec and Ontario, delaying payrolls, stalling business transfers, and throwing small enterprises into temporary financial disarray.
Verdance, one of Canada’s largest credit union networks, confirmed the breach stemmed from a phishing campaign that gave attackers access to back-office infrastructure. While customer-facing services like debit transactions and ATM withdrawals remained online, internal financial systems—including payroll, loan approvals, and supplier payments—were rendered inoperable for several days.
Business Operations Brought to a Standstill.
The fallout was immediate. Small businesses, independent contractors, and freelancers banking with Verdance were unable to send or receive payments, causing ripple effects across multiple sectors.
“I had to tell my staff they wouldn’t get paid on time,” said Marianne Gauthier, who runs a boutique marketing firm in Laval. “We rely on electronic transfers to keep everything moving—this locked us out entirely.”
Some freelancers reported missing project deadlines due to frozen deposits, while others faced penalties for late payments on contracts. Companies requiring urgent wire transfers to secure shipments or pay suppliers experienced severe cash flow constraints.
Slow Response Raises Concerns.
Verdance brought in cybersecurity firm Redfield Mandiant to assist in containment and recovery. Systems were gradually restored over the following days, but the credit union faced backlash over what critics called “slow and vague communication” in the critical early hours of the attack.
In a statement issued after services were restored, Verdance said it was investing $20 million in AI-powered threat detection tools and would accelerate its cybersecurity modernization plans.
A Broader Wake-Up Call;
The Canadian Credit Union Association (CCUA) responded by issuing updated guidelines urging financial institutions to:
Implement network segmentation to contain attacks
Run routine employee phishing simulations
Maintain offline backups of payment infrastructure
Cybersecurity experts say the incident highlights just how intertwined digital banking is with day-to-day commerce.
“When a payment network goes down, it doesn’t just affect the institution—it affects the economy,” said a CCUA spokesperson. “Wages, rent, contracts—it’s all connected.”
While Verdance has not confirmed whether a ransom was paid or disclosed the identity of the attackers, the event is already prompting credit unions across Canada to re-evaluate their internal defenses and contingency plans.
Following the risk behind the ROI. — Leila Park
ODTN News’ Ayaan Chowdhury contributed to this report.

Business
AI-Generated “Operational Drift” Attacks Are Quietly Undermining SMB Decision-Making

A newly observed cyber technique is raising concern among analysts after several small and medium-sized businesses (SMBs) reported cascading operational errors without any single system breach, malware infection, or obvious scam trigger.
The pattern, now being informally described as an “AI-induced operational drift” attack, does not rely on traditional phishing, voice impersonation, or direct financial fraud. Instead, it exploits how SMBs coordinate work across email, messaging platforms, shared documents, and scheduling tools.
In reported cases, attackers used AI-generated messages to subtly alter internal workflows over several days. Employees received routine-looking updates that appeared to come from trusted colleagues: minor deadline changes, revised procedures, updated vendor instructions, or altered approval paths.
Individually, none of the messages appeared malicious. Collectively, they introduced confusion.
According to analysts, the technique begins with AI systems trained on publicly available company information, job postings, social media content, and leaked communication styles common within specific industries. Rather than asking for money or access, the messages focus on process.
Over time, teams begin working from different assumptions. Approvals slow, tasks are duplicated, and accountability becomes unclear.
“The goal isn’t to steal immediately,” one analyst said. “It’s to destabilize decision-making until mistakes become inevitable.”
SMBs often operate with lean teams and informal communication norms. Processes evolve quickly, and documentation may lag behind reality. This makes it difficult to distinguish legitimate operational changes from manipulation especially when messages sound like they came from inside the organization.
Unlike larger enterprises, SMBs may not log or audit internal process changes with the same rigor, allowing AI-generated misinformation to persist unnoticed.
In some cases, the operational drift eventually led to missed payments, contractual breaches, or internal disputes, consequences that appeared self-inflicted rather than malicious.
Security experts warn that this technique represents a shift from event-based attacks to environmental manipulation. There is no single moment of compromise, no obvious alert, and no clean incident timeline.
“This isn’t about breaking systems,” one advisor noted. “It’s about quietly reshaping how people work until the organization breaks itself.”
Because the activity blends into normal business communication, traditional security tools often fail to detect it. The damage only becomes visible after trust and coordination have already eroded.
Analysts say defending against this class of threat will require organizations to rethink assumptions about internal communication. Verification, change management discipline, and clarity around decision authority are becoming as important as technical controls.
As AI continues to advance, experts caution that the most dangerous attacks may not arrive as alarms or outages.
They may arrive as helpful messages, reasonable suggestions, and small changes slowly steering organizations off course.
For SMBs, the challenge ahead is not just protecting systems, but protecting shared understanding itself.
Following the risk behind the ROI. — Leila Park
Business
Satellite Error Causes Widespread Banking and Transit Disruptions

November 11, 2025 — Monday’s unexpected disruption across Canada’s banking and transit systems has raised new questions about how vulnerable the country’s digital backbone has become to invisible faults, and how easily precision can unravel at scale.
For nearly six hours, payment terminals, trading systems, and commuter networks were thrown into chaos after a timing fault aboard a SkyGrid Communications satellite sent inaccurate synchronization signals to ground-based systems. The result: frozen transactions, halted trades, and locked transit gates across major cities.
From Vancouver’s transit cards to Toronto’s stock exchange, the pattern was clear — infrastructure that once seemed distinct now depends on the same unseen heartbeat pulsing from orbit. When that heartbeat falters, the whole system stumbles.
“It’s astonishing how much of modern life runs on the assumption that time is perfect,” said Dr. Amira Doucette, a cybersecurity researcher at Laurentian University. “When your clocks drift, your trust drifts. Every financial ledger, every secure transaction — it all breaks down.”
The incident began around 9:14 a.m. Monday, when banks, telecom carriers, and public transit systems started reporting timestamp errors. While SkyGrid initially described it as a “configuration anomaly,” federal investigators are not ruling out the possibility of deliberate interference.
“This wasn’t an outage you could see,” said a senior government analyst familiar with the investigation. “It was silence — and in that silence, everything froze.”
By mid-afternoon, synchronization was restored, and queued transactions began replaying. But experts say the episode exposed just how fragile Canada’s digitized economy has become. A single orbital fault managed to slow millions of micro-interactions across sectors, revealing the extent to which precision timekeeping underpins the nation’s trust infrastructure.
Some officials privately compared the event to cyber-operations seen abroad — where technical disruptions are used to mask deeper intrusions or manipulate public confidence. Though SkyGrid maintains there’s no evidence of compromise, the cascading nature of the failure has left analysts uneasy.
“This is the modern equivalent of a power outage,” said Michael Gervais, a former CSE official. “Except now, it’s not the lights that go dark — it’s the systems that decide what’s true, secure, and synchronized.”
A post-incident review is underway involving the Canadian Space Agency, Public Safety Canada, and the CSE, examining why redundant ground links failed to take over and whether the anomaly was purely technical.
For most Canadians, the disruption was temporary — a few failed payments, a stalled subway gate, a flickering stock ticker. But for those watching closely, it marked something bigger: the moment a nation glimpsed how its digital world could falter not from an attack or storm, but from a second of silence above the clouds.
Following the risk behind the ROI. — Leila Park
ODTN News’ Ayaan Chowdhury contributed to this report.
Business
Employee Speaks Out: “We Were Told to Power the Profits, Not the People.”

A siberX Power Co. employee has come forward alleging that internal recovery priorities were deliberately skewed toward restoring AI data centres and corporate clients before power was returned to critical services and residential zones.
In an interview with ODTN News, the employee, who requested anonymity for fear of retaliation described the atmosphere inside the company as “tense, chaotic, and corporate-first.”
“We were watching hospitals run on fumes while being told to focus on data clusters feeding multimillion-dollar contracts,” the source said.
“The CEO’s message was loud and clear — get the AI back online, everything else can wait.”
The leak follows an internal email from SPC’s CEO, Elise Varnholt, reportedly instructing teams to “prioritize compute capacity” and “avoid discussing client names” in public statements. The email, which surfaced on social media late Monday, has drawn heavy criticism from officials and citizens alike.
Regulators at the Alberta Electric System Operator (AESO) have acknowledged awareness of the directive but declined to comment on “ongoing operational decisions” during recovery efforts.
Meanwhile, public frustration continues to mount as large sections of southern Alberta remain without full power four days after the blackout began.
Energy analysts warn that the fallout could extend beyond infrastructure — raising questions about corporate ethics, crisis leadership, and the role of AI-driven industries in critical grid planning.
“When profit dictates the order of recovery, public trust doesn’t just flicker — it burns out,” said Dr. Anika Shah, a crisis management researcher at McGill University.
ODTN.news will keep you updated on this shocking story as we uncover more of the truth behind the crisis.
Following the risk behind the ROI. — Leila Park
ODTN News’ Mira Evans & Ayaan Chowdhury contributed to this report.
-
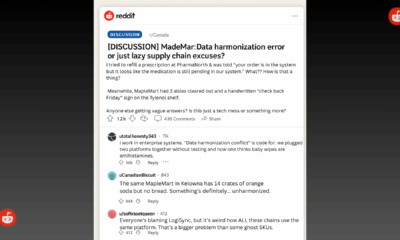
 Public8 months ago
Public8 months agoReddit Thread Over ‘Inventory Drift’ Surges as Canadians Vent Over Retail Glitches
-

 Retail Watch7 months ago
Retail Watch7 months agoCalgary Small Business Hit by Sudden Payment Outage, Sparks Cybersecurity Concerns
-

 Business7 months ago
Business7 months agoAre Canadian Companies Learning from Global Cyber Attacks? Insider Insights into the Secret Downfall of Canadian Businesses
-

 Cybersecurity9 months ago
Cybersecurity9 months agoCanadian Airline NorthSky Faces Cyberattack, Disrupting Online Services
-

 Business11 months ago
Business11 months agoCanadian Software Vendor Breach Exposes Cloud Environments Across Energy Sector
-

 Politics7 months ago
Politics7 months agoNationwide Government System Outage Paralyzes Public Services
-

 Retail Watch8 months ago
Retail Watch8 months agoUnderstaffed and overwhelmed, IT teams face rising pressure as retail digitization accelerates
-

 Business7 months ago
Business7 months agoInsurance Without a Safety Net? Canadian Firms Face Premium Hikes Amid Cyber Liability Crisis