Cybersecurity
The Black Signal — How a Cyberattack Shut Down Ebonia’s Power Grid in Minutes

Meridian, Ebonia —
The lights went out across central Ebonia just after 7:00 p.m. on December 23, 2024.
More than a quarter-million residents in the country of Ebonia suddenly lost power as substation after substation dropped offline. What initially looked like a catastrophic technical failure was, in fact, the result of a coordinated cyberattack on the national grid’s SCADA infrastructure—the first confirmed case of a cyber operation triggering a real-world blackout.
The attackers had breached EbonGrid’s internal corporate systems months earlier using a phishing campaign that delivered an advanced malware package later dubbed Black Signal. From there, they moved laterally through the utility’s network until they reached its Industrial Control System (ICS) environment, which governs the core components of grid operations, including substations, circuit breakers, and load balancing.
Investigators later confirmed that the attackers gained persistent access to several SCADA terminals used by regional control centers. On the night of the attack, the malware initiated a sequence of remote commands that disabled dozens of substations in under seven minutes.
“Operators watched as the interface was hijacked in real time,” said a former EbonGrid engineer who was present during the event. “We couldn’t override it. The SCADA terminals just stopped responding, and our entire substation cluster began to collapse.”
Making matters worse, a secondary payload wiped historical logs and corrupted firmware on field devices, delaying diagnostics and manual recovery. Engineers were forced to physically dispatch crews to dozens of affected sites, as out-of-band communication and telemetry feeds were either compromised or completely down.
Power wasn’t fully restored until midday on December 24.
In the days following the attack, Ebonia’s Ministry of Energy issued a muted statement referring to the blackout as “a deliberate intrusion into critical infrastructure.” No group formally claimed responsibility, but intelligence sources pointed to a well-resourced threat actor believed to be operating from Eastern Europe.
The attack marked a turning point in cybersecurity history. It was the first time malware had been used to directly manipulate SCADA systems at scale, triggering a kinetic, cross-sector disruption that affected not just electricity but also emergency services, rail signaling, telecom towers, and regional banking systems relying on stable power.
Global energy providers took immediate notice. ICS and SCADA security audits were fast-tracked in countries across North America, Europe, and Southeast Asia. “It was a wake-up call,” said Dr. Henrick Voss, a grid security analyst at the Nordhaven Institute. “Everyone realized that you don’t need to bomb a power station to shut it down anymore. You just need a password, some patience, and the right code.”
The Ebonia incident remains one of the most studied cyber-physical attacks in modern history—a case study in how digital pathways can be weaponized to bring down physical infrastructure in seconds.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury

Cybersecurity
Luxury Resort & Casino Hit by Ransomware, Employee HR Systems Compromised

February 25, 2026 — Luxury hospitality and gaming operator Silver Court Resorts confirmed late Tuesday night that a cyber intrusion led to the compromise of sensitive employee data, following what investigators describe as a quiet, multi-stage attack that unfolded over several weeks.
The attackers are demanding 21.8 BTC (≈ $1.6M CAD) in exchange for not publishing what they claim is more than 600GB of internal HR and payroll data. While guest booking systems, casino floors, and payment platforms remain operational, internal HR infrastructure has been taken offline as forensic teams continue containment efforts.
According to sources familiar with the investigation, the breach did not begin with ransomware. It began with credentials.
Timeline of the Intrusion
January 29 – Security logs show anomalous authentication attempts against Silver Court’s legacy VPN gateway.
January 31 – Successful login from an IP address previously linked to an infostealer malware campaign. Analysts believe credentials were harvested from a finance department employee whose laptop had been infected with a commodity infostealer strain.
February 2 – Attackers deploy a legitimate Remote Monitoring & Management (RMM) tool to establish persistence. The tool blended into normal administrative traffic.
February 4–10 – Lateral movement observed toward payroll and HR file servers. Privilege escalation achieved via misconfigured service account with domain admin rights.
February 12 – Large outbound data transfer (≈ 600GB) flagged but not immediately escalated.
February 14 – Ransom note discovered on internal HR systems.
Preliminary forensic analysis indicates that the compromised data includes employee names and addresses, Social Insurance Numbers, payroll records, direct deposit banking details, benefits enrollment information, and internal HR case documentation. Security officials state that no customer payment systems were directly accessed; however, investigators caution that employee PII breaches often become stepping stones for broader fraud operations.
Threat intelligence analysts warn that exposures of this nature frequently precede identity theft campaigns, business email compromise attempts, credential stuffing against internal and customer portals, and highly targeted social engineering attacks aimed at executives and finance teams.
Incident responders believe the attack chain began months earlier when credentials were harvested through an infostealer infection. From there, an unpatched VPN appliance allowed password-based access into the corporate network. Although MFA was reportedly enabled across most systems, it was not enforced on the legacy gateway used in the intrusion. Attackers then leveraged a legitimate RMM tool to maintain access and avoid traditional malware detection. Domain misconfigurations, including a service account with domain administrator privileges, enabled rapid privilege escalation once inside.
“This wasn’t flashy,” said one responder involved in the containment effort. “It was patient. Controlled. Each step looked normal on its own. The danger was in how the pieces fit together.”
The threat group, identifying itself as “Black Meridian,” has posted a countdown timer on a Tor-based leak site, claiming it will release employee payroll data within seven days if the ransom is not paid. The organization has not confirmed whether negotiations are underway, stating only that it is working with external forensic teams and law enforcement partners.
The incident underscores a recurring reality across the hospitality and gaming sector: when revenue platforms are hardened and segmented, attackers often pivot to internal systems where monitoring thresholds are lower and data is dense. HR environments, in particular, remain one of the most concentrated repositories of high-value information inside an enterprise.
In today’s threat landscape, attackers do not always go straight for customers. They start with the people behind the business.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
Cybersecurity
New Year’s Day Cloud Disruption at Kestralyn Solutions Exposes Gaps in Automation Oversight

A service disruption at Kestralyn Solutions, a Canadian company that provides cloud-based software used by businesses to manage supply chains, inventory, and delivery operations, unfolded on New Year’s Day, a period when many staff were on holiday and routine monitoring was operating under reduced coverage.
According to information reviewed by ODTN News, the incident followed a scheduled update to an automated cloud workflow responsible for managing infrastructure scaling and system health. The change was implemented through standard processes late on December 31 and initially appeared to function as expected.
In the early hours of January 1, customers began experiencing intermittent service disruptions and delayed system responses. Internal automation processes behaved inconsistently across regions, but with limited staff on duty, the issue was not immediately recognized as a systemic failure.
Investigators later determined the disruption was not the result of unauthorized access or malicious activity. Instead, a conflict between automated scaling logic and existing resource governance policies caused infrastructure resources to cycle repeatedly. The activity was technically valid and generated no security alerts, allowing the issue to persist longer than it otherwise might have during normal operating hours.
Operations teams on call initially interpreted the issue as a temporary performance fluctuation, a common occurrence during holiday traffic shifts. Without clear indicators of a broader control-plane failure, escalation was delayed until full staffing levels resumed later in the day.
By the time engineers isolated and corrected the automation workflow, multiple customer-facing services had been affected. The company later confirmed there was no data compromise but acknowledged that reduced staffing and limited cross-team visibility contributed to the delayed response.
Industry analysts say incidents occurring during holidays and long weekends are increasingly common, as cloud environments continue to operate at full scale even when organizations do not. Automation, while essential for managing modern infrastructure, can amplify small configuration issues when human oversight is limited.
The New Year’s Day incident at Kestralyn highlights a broader operational challenge facing many organizations. As reliance on cloud automation grows, preparedness can no longer assume full staffing or ideal conditions. Systems fail on holidays, during weekends, and in the early hours often when teams are least equipped to respond quickly.
For organizations entering 2026, the lesson is not simply about improving security controls, but about ensuring resilience during the moments when attention is lowest and systems are expected to run on their own.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
Cybersecurity
“This Isn’t Over” A Warning That Closed Out 2025

What began as a city-wide transit outage on December 4th has now become one of the most unsettling closing chapters of 2025.
As systems were gradually restored and commuters returned to platforms across the city, ODTN News received an anonymous message through its secure tip line. The message was brief, unverified, and deeply concerning:
“This isn’t over.”
Authorities have not confirmed the source of the message, nor whether it is directly linked to the transit disruption. But in the context of the past year, the warning has struck a nerve across the cybersecurity and emergency preparedness community.
The transit outage was not an isolated event. Throughout 2025, Canada experienced a string of disruptive incidents affecting critical systems once assumed to be resilient:
-
Power grid instability impacting multiple regions
-
Supply chain disruptions causing shortages and delays
-
Transit shutdowns that stranded thousands of commuters
-
Cascading technology failures that blurred the line between cyber and physical risk
Individually, each incident was treated as manageable. Collectively, they tell a different story…one of systems under sustained pressure, probing, and stress.
Several experts have raised concerns that these events resemble testing behaviours, where attackers observe response times, communication breakdowns, and public reaction rather than seeking immediate destruction.
Security analysts warn that the most dangerous outcome is not the attacks themselves, but the normalization of disruption.
“Each time we recover without meaningful reflection or preparation, we signal that disruption is acceptable,” said one crisis response advisor familiar with multiple 2025 incidents. “That’s what invites escalation.”
While investigations continue into the December transit outage, there is growing concern that Canada’s focus has leaned too heavily on response, restoring services quickly without equal investment in training, coordination, and realistic crisis preparation.
Across government agencies, private operators, and critical infrastructure providers, one issue keeps surfacing: many teams are encountering these scenarios for the first time during the crisis itself.
Experts argue that tabletop exercises, simulations, and cross-sector drills are no longer optional. They are essential tools to expose gaps before real-world consequences unfold.
Crisis preparation isn’t about predicting the exact next incident. It’s about ensuring leaders, operators, and communicators know how to function when uncertainty is high, information is incomplete, and public trust is on the line.
The anonymous message sent to ODTN News remains under review. Whether it was a provocation, a bluff, or something more deliberate is still unknown.
What is known is this: 2025 has revealed how interconnected and vulnerable Canada’s systems have become. Power, transit, supply chains, and digital infrastructure no longer fail in isolation. When one stumbles, others feel the impact.
As the country moves into 2026, the question is no longer if another disruption will occur, but whether organizations will be better prepared when it does.
Because if the message is true, if this really isn’t over then training, coordination, and crisis readiness may be the difference between disruption and disaster.
Watching the perimeter — and what slips past it. — Ayaan Chowdhury
-
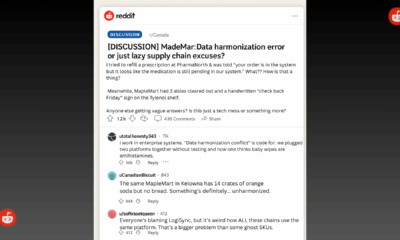
 Public8 months ago
Public8 months agoReddit Thread Over ‘Inventory Drift’ Surges as Canadians Vent Over Retail Glitches
-

 Business7 months ago
Business7 months agoAre Canadian Companies Learning from Global Cyber Attacks? Insider Insights into the Secret Downfall of Canadian Businesses
-

 Retail Watch7 months ago
Retail Watch7 months agoCalgary Small Business Hit by Sudden Payment Outage, Sparks Cybersecurity Concerns
-

 Cybersecurity9 months ago
Cybersecurity9 months agoCanadian Airline NorthSky Faces Cyberattack, Disrupting Online Services
-

 Business11 months ago
Business11 months agoCanadian Software Vendor Breach Exposes Cloud Environments Across Energy Sector
-

 Retail Watch8 months ago
Retail Watch8 months agoUnderstaffed and overwhelmed, IT teams face rising pressure as retail digitization accelerates
-

 Politics7 months ago
Politics7 months agoNationwide Government System Outage Paralyzes Public Services
-

 Business7 months ago
Business7 months agoInsurance Without a Safety Net? Canadian Firms Face Premium Hikes Amid Cyber Liability Crisis